Innovative Ways of Getting Into a Building with a Intercom System
As technology advances, building access control methods continue to evolve, providing convenience, security, and efficiency to residents and property managers. Intercom systems are a staple for multi-unit residential buildings and commercial properties, serving as the gatekeepers for granting or denying access. This article will explore five modern ways to get into a building equipped with an intercom system, including face recognition, keypad entry, Mifare keyfobs, NFC and Bluetooth readers, and smartphone-based keyless entry.
Face Recognition
Face recognition is a cutting-edge biometric technology that allows authorized individuals to access a building without needing a physical key. This system works by capturing and analyzing facial features, comparing them to a pre-established database of authorized users. Once the system verifies the individual’s identity, it grants access. Face recognition boasts high levels of security, as it is challenging to spoof, and eliminates the risk of lost or stolen keys. It also provides a touchless, hygienic solution in times where health concerns are a priority.
Keypad Entry

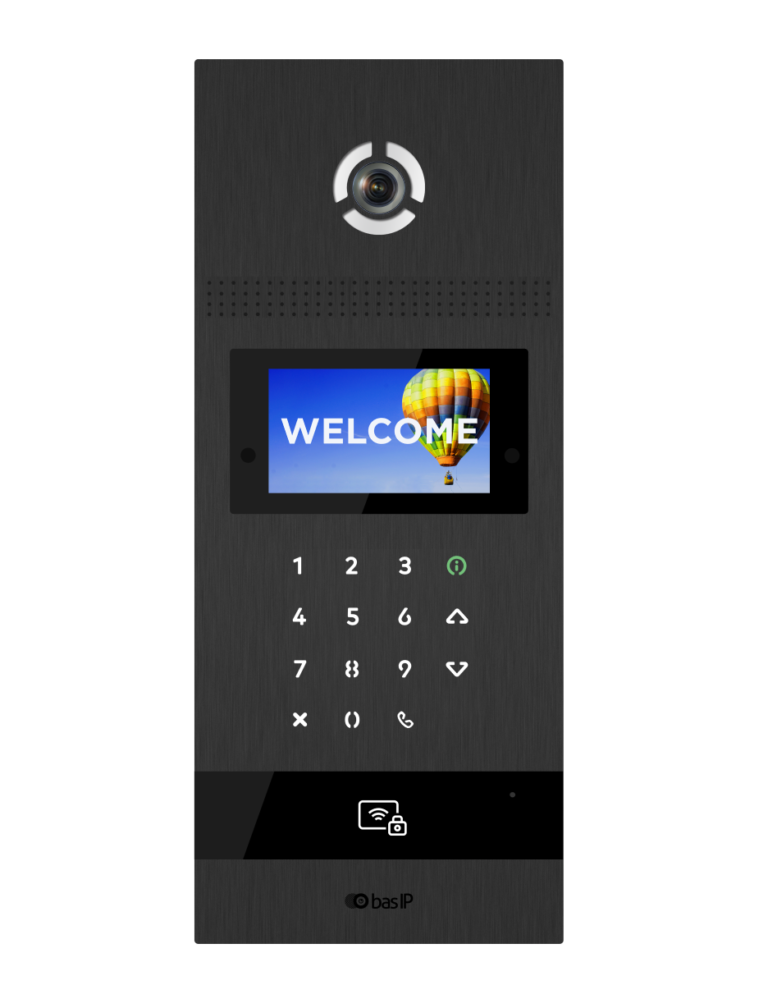
Keypad entry systems are a more traditional but still highly effective method for secure access. Users input a unique code on a numeric keypad installed near the building’s entrance. Upon correct code entry, the system unlocks the door, allowing access. Keypad entry is straightforward to use and cost-effective. Additionally, property managers can easily change or update access codes, providing flexibility when dealing with tenant turnovers, temporary access for maintenance personnel, or enhanced security.
Mifare Keyfobs
Mifare keyfobs are compact, durable, and contactless smart card technology. They use radio frequency identification (RFID) to communicate with the intercom system. When the user presents the keyfob near the reader, the system authenticates the embedded information and grants access. Mifare keyfobs are resistant to wear and tear, as they have no moving parts, and offer a high level of security with unique encryption keys. They are a popular choice for apartment buildings and commercial properties, where numerous users require access at different times.



NFC and Bluetooth Readers
Near Field Communication (NFC) and Bluetooth readers are wireless access control methods that take advantage of the technology available in most modern smartphones. NFC operates within a short range (typically a few centimeters), while Bluetooth works over a more extended range (up to several meters). Both systems require the user’s smartphone to be in proximity to the reader to unlock the door.
NFC and Bluetooth readers offer many advantages, such as the ability to grant temporary or time-limited access to guests or service providers, eliminating the need for physical keys. Property managers can track and monitor access in real-time, ensuring enhanced security. Additionally, these systems can be integrated with other smart building applications, such as energy management or home automation systems.
Keyless Entry with Smartphone
Smartphone-based keyless entry systems are a convenient and secure option for accessing buildings with intercom systems. With this method, authorized users install an app on their smartphone, which acts as a virtual key. When the user approaches the door, the system recognizes the smartphone’s unique identifier and grants access.
This method provides several benefits, including easy management of user permissions by property managers and the ability to grant temporary access to guests or service providers. Moreover, users do not need to carry additional devices, such as key cards or fobs, as their smartphone serves as the key.
Conclusion
In an era where convenience, security, and technology go hand in hand, various methods are available to access a building with an intercom system. Face recognition, keypad entry, Mifare keyfobs, NFC and Bluetooth readers, and smartphone-based keyless entry systems offer unique advantages and make your daily life easier and more securer.