Best Visitor Log Software: Elevating Intercom Efficiency

As BAS-IP, a leader in IP intercom systems manufacturing, we’re at the forefront of integrating cutting-edge technologies. Today, we’re exploring how visitor log software is revolutionizing the intercom landscape, offering unprecedented security and operational efficiency.
Table of Contents
Understanding Visitor Log Software
What is Visitor Log Software?
In the digital era, visitor log software is the cornerstone of modern intercom systems. It’s a sophisticated tool designed to digitally record, track, and manage visitor information. This technology replaces the traditional pen-and-paper logbooks, offering a more secure, efficient, and accessible way to handle visitor data. It’s not just about recording names; it’s about creating an intelligent, interactive system that enhances overall security and user experience.
Key Features of Visitor Log Software
Automated Visitor Tracking
This feature is the heart of visitor log software. It allows for the real-time tracking of visitors, recording their entry and exit times, duration of stay, and even the purpose of their visit. This automation reduces human error and enhances the accuracy of visitor data.
Integration Capabilities
One of the most significant advantages of modern visitor log software is its ability to integrate seamlessly with existing security and intercom systems. This integration can range from simple data sharing to more complex interactions like activating doors or elevators for authorized visitors.
Real-time Alerts
Security is paramount in any visitor management system. Real-time alerts are crucial for immediate response to potential security breaches. These alerts can be customized based on specific criteria such as unauthorized access attempts or visitors overstaying their welcome.
User-Friendly Interface
The best visitor log software comes with an intuitive, easy-to-navigate interface. This ensures that both staff and visitors can use the system with minimal training, making the process of visitor management as smooth as possible.
Customizable Visitor Experience
From pre-registration features to personalized greetings, visitor log software can be tailored to provide a unique experience for each visitor. This customization not only improves visitor satisfaction but also reflects positively on the organization’s brand.
Data Analytics and Reporting
With the wealth of data collected, visitor log software often includes analytics and reporting capabilities. This feature allows organizations to analyze visitor patterns, peak times, and other valuable insights, which can be used to improve security measures and operational efficiency.
Benefits of Visitor Log Software in Intercom Systems
Enhanced Security and Monitoring
Event Logging
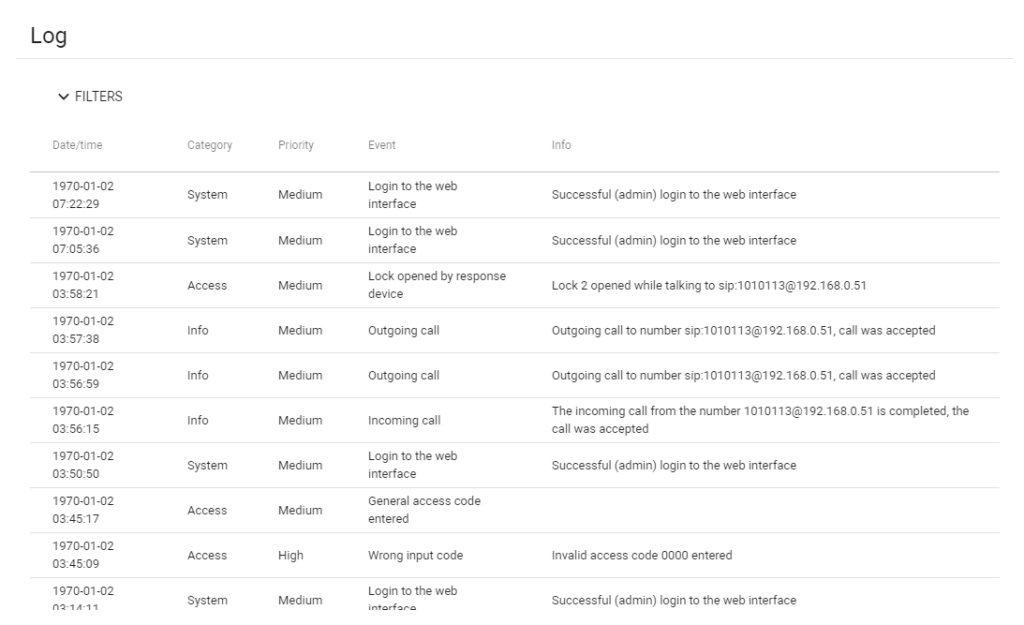
The software logs various events such as login attempts (both successful and failed), incoming and outgoing calls, and emergency events. This comprehensive logging ensures that all activities are monitored, enhancing the security of the premises.
Access Control
It records events related to access control, like access granted by the web interface or remote server, lock openings by response devices or identifiers, and general access code entries. This feature ensures that only authorized individuals can access the premises, thereby enhancing security.
Efficient Management and Operation
Real-Time Alerts
The software provides real-time alerts for critical events like emergency situations, tamper triggers, or prolonged lock openings. This allows for immediate response to potential security threats.
Data Management
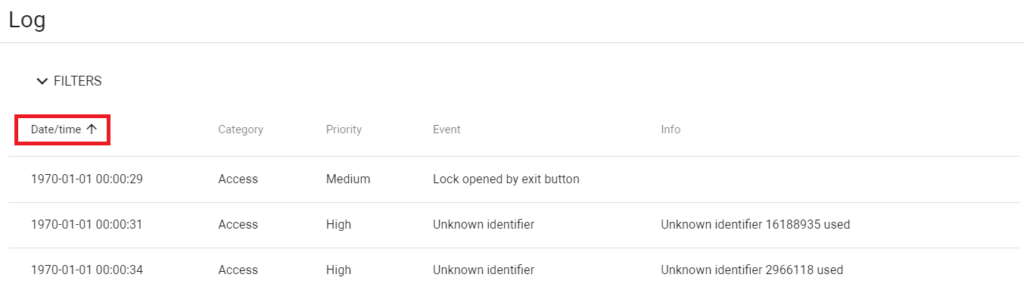
With the ability to sort and filter events by date, category, event, and priority, managing and reviewing logs becomes more efficient, aiding in quick decision-making and analysis.
Customizable and User-Friendly Interface
Flexible Data Display and Quick Search
The software offers a user-friendly interface with customizable filters for sorting and searching events. This enhances the user experience and makes it easier to find specific information quickly.
Compliance and Reporting
Detailed Event Categories
The software categorizes events into different priorities (low, medium, high, emergency, critical) and types (system, access, emergency), which aids in compliance reporting and security audits.
Detailed Chart of Visitor Log Software Features
| Feature Category | Specific Feature | Description |
|---|---|---|
| Security and Monitoring | Event Logging | Logs all panel-related events including system logins, calls, and emergency events. |
| Access Control | Records access-related events, ensuring only authorized access. | |
| Management and Operation | Real-Time Alerts | Provides instant alerts for critical security events. |
| Data Management | Allows sorting and filtering of events for efficient management. | |
| User Interface | Customizable Filters | Offers flexible data display and quick search options. |
| Compliance and Reporting | Detailed Event Categories | Categorizes events for easy reporting and compliance. |
The BAS-IP visitor log software not only provides robust security features but also ensures efficient operation and management, making it an invaluable tool in modern intercom systems.
Choosing the Right Visitor Log Software

When it comes to enhancing intercom systems with visitor log software, selecting the right solution is crucial. Here’s a guide to making an informed decision, culminating in the conclusion that BAS-IP offers the best visitor log software available.
Factors to Consider
- Compatibility with Existing Systems: Ensure the software seamlessly integrates with your current intercom setup. This avoids the need for extensive modifications or replacements.
- Scalability: The software should be able to grow with your needs. Whether you’re managing a small office building or a large complex, scalability is key.
- User Experience: Consider the ease of use for both administrators and visitors. A user-friendly interface reduces training time and enhances overall satisfaction.
- Security Features: Robust security features are non-negotiable. Look for software that offers comprehensive monitoring and real-time alerts.
- Customization Options: Every organization has unique needs. Customizable software can adapt to specific requirements, from visitor check-in processes to data reporting.
- Support and Maintenance: Reliable customer support and regular software updates are essential for long-term functionality and security.
Comparison of Visitor Log Software Solutions
While there are several options on the market, a comparison reveals that BAS-IP’s visitor log software stands out for several reasons:
BAS-IP Software
Known for its advanced integration capabilities, BAS-IP software excels in compatibility with a wide range of intercom systems. Its scalability makes it suitable for various sizes and types of buildings. The intuitive user interface ensures a smooth experience for both administrators and visitors. Security features are top-notch, with detailed event logging and real-time alerts. The software is highly customizable, allowing for tailored visitor management solutions. Additionally, BAS-IP’s commitment to customer support and regular updates makes it a reliable choice.
Other Solutions
While other software solutions may offer some of these features, they often fall short in areas like scalability, customization, or user experience. Some may not integrate as seamlessly with existing systems, or they might lack in terms of robust security features.
Future Trends in Visitor Log Software
The landscape of visitor log software is continuously evolving, driven by technological advancements and changing security needs. As we look towards the future, several key trends are set to shape the development of visitor log software, particularly in the context of intercom systems.
Integration of Advanced Technologies
- Artificial Intelligence (AI) and Machine Learning: AI and machine learning algorithms are expected to play a significant role in visitor log software. They can enhance predictive analytics, automate visitor identification processes, and improve anomaly detection, leading to more proactive security measures.
- Internet of Things (IoT): The integration of IoT devices with visitor log software will enable more interconnected security systems. IoT devices like smart locks, cameras, and sensors can feed real-time data into the visitor log system, allowing for more responsive and adaptive security protocols.
- Facial Recognition and Biometrics: The use of biometric technologies, such as facial recognition, fingerprint scanning, and iris recognition, will add an extra layer of security. These technologies can streamline the visitor check-in process while ensuring that access is granted only to verified individuals.
Enhanced Data Analytics and Reporting
- Predictive Analytics: Future visitor log software will likely incorporate more advanced predictive analytics capabilities. By analyzing historical data, the software can predict peak visitor times, potential security threats, and maintenance needs, allowing for better resource allocation and planning.
- Customized Reporting: As organizations become more data-driven, the demand for customized reporting features in visitor log software will increase. These reports will provide insights into visitor patterns, security incidents, and system performance, aiding in strategic decision-making.
User Experience and Accessibility
- Mobile Integration: The integration of visitor log software with mobile applications will enhance user accessibility. Features like mobile check-ins, digital passes, and remote access control will provide a more convenient and efficient experience for both visitors and administrators.
- Voice-Activated Controls: The incorporation of voice recognition and voice-activated controls will make visitor log software more accessible and user-friendly, especially for individuals with disabilities or those who prefer hands-free operation.
Sustainability and Eco-Friendly Solutions
- Energy-Efficient Operations: Future developments in visitor log software will likely focus on sustainability. This could include optimizing system operations to reduce energy consumption and integrating with eco-friendly building management systems.
- Paperless Solutions: The move towards paperless operations will continue, with digital visitor logs and electronic documentation becoming the norm. This not only enhances efficiency but also supports environmental sustainability.
Case Studies
The real-world impact of visitor log software in intercom systems can be best understood through case studies. These examples illustrate how different organizations have implemented visitor log solutions, highlighting the benefits and transformations experienced.
| Case Study | Setting | Challenge | Solution | Key Outcomes |
|---|---|---|---|---|
| Case Study 1: Corporate Office Building | Large corporate office with high visitor traffic | Inefficient manual sign-in process leading to delays and errors | Implementation of BAS-IP’s visitor log software integrated with existing intercom and access systems | – Streamlined check-in process, reducing time by 50% – Enhanced building security with real-time monitoring – Valuable data insights for better resource allocation |
| Case Study 2: Residential Complex | High-end residential complex | Need for improved security and convenience in visitor management | BAS-IP’s visitor log software integrated with IP intercom system, allowing remote access management via mobile app | – Increased resident satisfaction due to convenient remote access management – Secure, traceable record of all visitors enhancing safety – Reduced administrative workload for front desk staff |
| Case Study 3: Educational Institution | University campus | Managing visitor flow during events and maintaining campus security | BAS-IP’s visitor log software with features like pre-registration for events and instant security alerts | – Efficient management of visitors during large events – Improved campus security with real-time monitoring – Comprehensive reporting for security audits and compliance |
Conclusion
As we’ve explored the various facets of visitor log software, from its key features and benefits to real-world applications, it’s clear that this technology is not just an add-on but a transformative tool for intercom systems. The case studies of a corporate office building, a residential complex, and an educational institution vividly illustrate the software’s versatility and its ability to adapt to diverse environments and needs.
Key Takeaways
- Enhanced Security and Efficiency: Visitor log software significantly improves security by providing real-time monitoring and data-driven insights. It streamlines the visitor management process, making it more efficient and less prone to errors.
- Adaptability and Integration: The software’s ability to integrate seamlessly with existing intercom and security systems makes it a versatile solution for various settings, from corporate to residential to educational.
- User Experience and Satisfaction: By simplifying the visitor check-in process and offering customizable features, visitor log software enhances the experience for both visitors and administrators, leading to increased satisfaction.
- Future-Ready Technology: With the integration of advanced technologies like AI, IoT, and biometrics, visitor log software is poised to become even more sophisticated, offering smarter and more secure visitor management solutions.
In conclusion, whether for a corporate office, a residential complex, or an educational institution, BAS-IP’s visitor log software represents the pinnacle of innovation and efficiency in visitor management. Its transformative impact on intercom systems is a testament to the power of technology in enhancing security, efficiency, and user experience in various settings.