RFID Key Management Systems: Superior Access Control
The Radio Frequency Identification (RFID) Key Management System emerges as a standout solution. This technology not only reinforces security but also optimizes efficiency in various industries.
Understanding RFID Technology
Radio Frequency Identification or RFID is a cutting-edge technology that uses electromagnetic fields to identify and track tags attached to objects. This technology ranges from low-frequency systems, high-frequency systems, to ultra-high-frequency systems, each with specific applications and advantages.
Key Management in Access Control
Key management in access control refers to the systematic administration of keys within an organization. An efficient key management system bolsters security and minimizes risk by ensuring that only authorized individuals have access to specific areas.
RFID Key Management
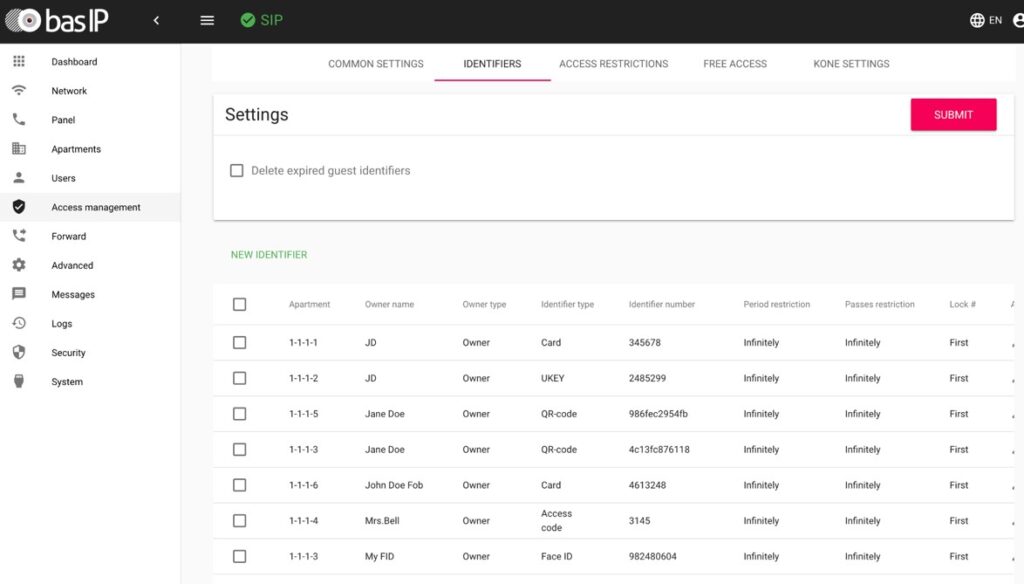
An RFID Key Management System is an advanced key management solution for RFID access control. It comprises an RFID reader, RFID tags, and a management software. By automating key tracking and management, these systems offer unparalleled security and convenience.
Benefits of RFID Key Management System
The RFID Key Management System comes with numerous benefits. It enhances security, promotes efficiency and productivity, and is cost-effective. Moreover, it provides traceability, promoting compliance and accountability.
Fast Creation of Temporary RFID Keys
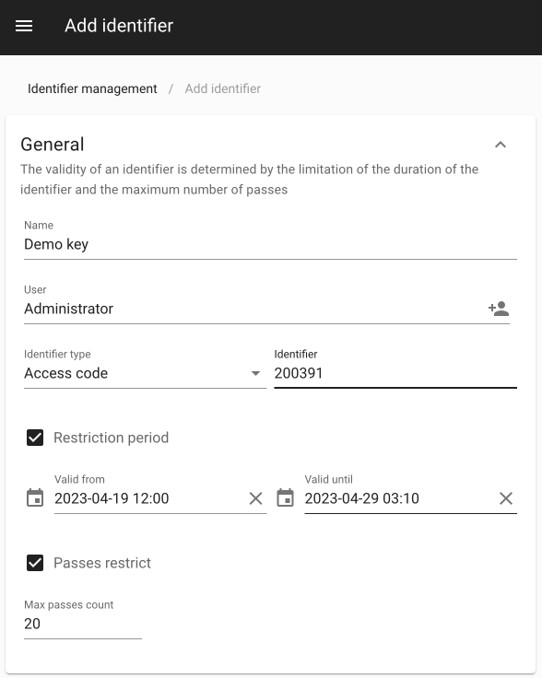
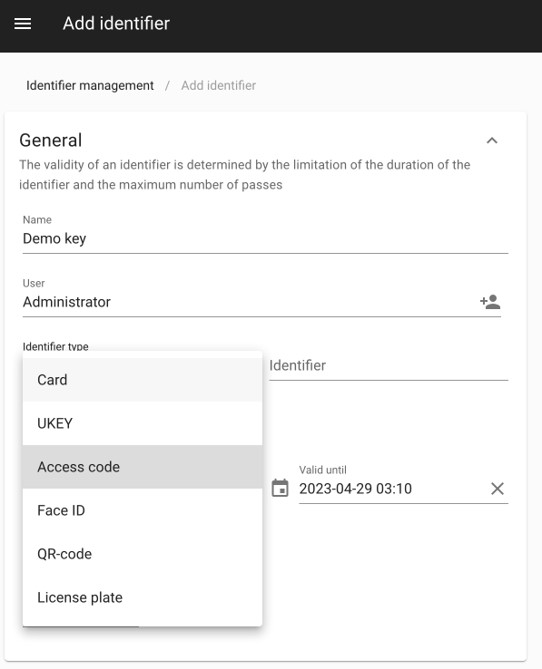
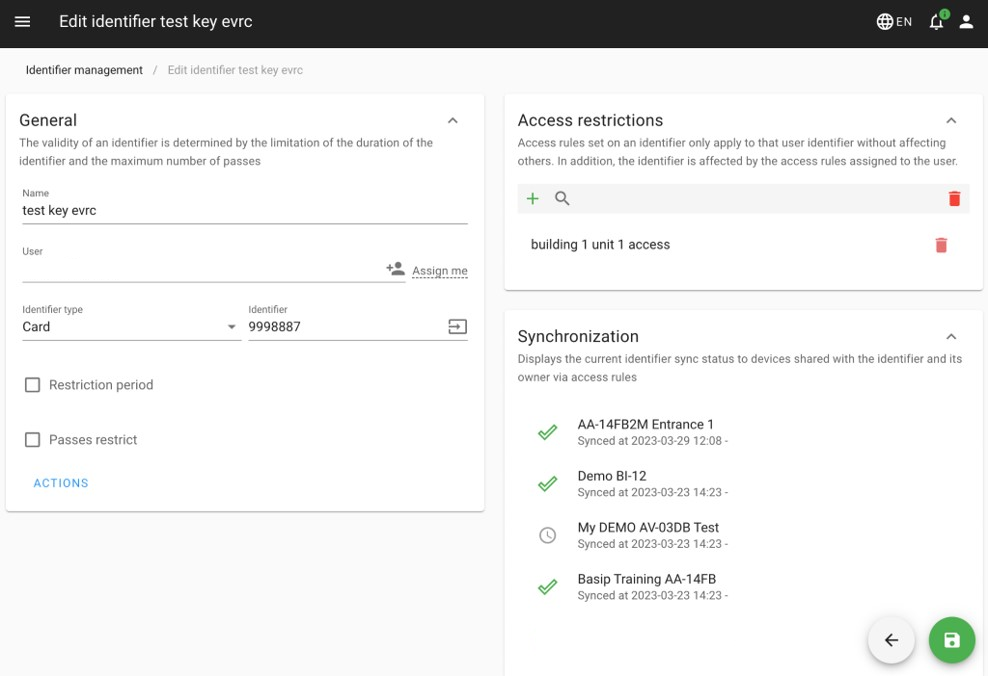
One of the standout features of BAS-IP Link is its ability to swiftly create temporary RFID keys. This feature is particularly valuable in situations where temporary access needs to be granted to visitors, contractors, or service providers. With just a few clicks, authorized personnel can generate temporary RFID keys with designated time frames, ensuring controlled and efficient access management.
Different Admin Roles for Effective Management
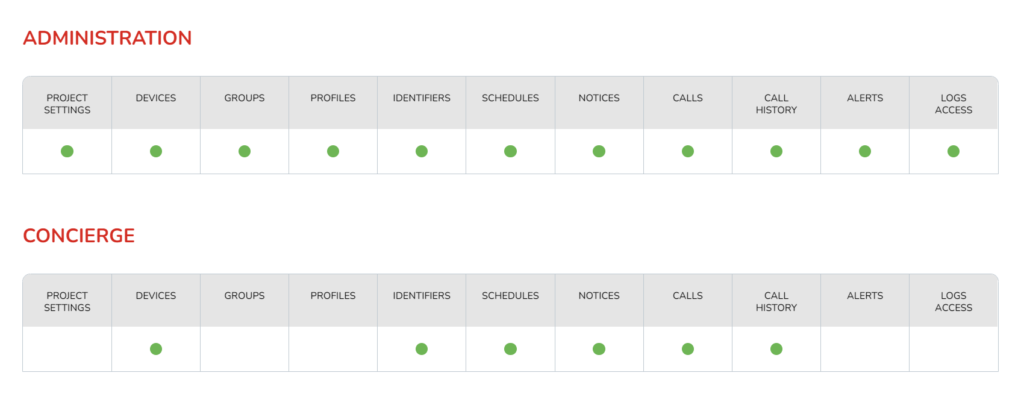
BAS-IP Link incorporates the concept of different admin roles, including Administrator and Concierge. Each role has its own set of administration options and access privileges within the system.
- Administrator: The Administrator has full control and can create objects of any size and structure within the system. They can form these objects into groups and grant various rights to Concierges and Users within these groups. The Administrator has the highest level of authority and can manage the overall system configuration.
- Concierge: The Concierge, also known as the Manager, is granted access and management rights by the Administrator. They have the ability to manage the assigned equipment and functionality within their designated area of responsibility. This includes tasks such as granting or revoking access, monitoring system activity, and managing specific access control features.
Enhanced Security
RFID Key Management Systems contribute significantly to the overall security of a premise. By utilizing encrypted data transmission, these systems prevent unauthorized access to restricted areas, making it nearly impossible for potential intruders to replicate or forge RFID keys. Additionally, each RFID key can be uniquely programmed, allowing for personalized access rights and traceability of each key.
Improved Efficiency and Productivity
Manual tracking of physical keys can be a laborious and time-consuming task. With an RFID Key Management System, key tracking becomes automated, reducing human errors and freeing up personnel to focus on other critical tasks. It can also streamline processes such as routine inspections, inventory checks, and more.
Cost-Effectiveness
While the upfront cost of implementing an RFID Key Management System might seem high, the long-term savings it brings can be substantial. The automation of key management significantly reduces the need for continuous replacement of lost or misplaced keys. Additionally, the prevention of unauthorized access can save a business from potential losses linked to theft or property damage.
Compliance and Accountability
In some industries, such as healthcare, manufacturing, and education, compliance with certain security standards is not just essential—it’s legally required. An RFID Key Management System provides detailed access logs, enabling organizations to demonstrate compliance with these regulations. Moreover, by tracking who accessed what areas at which times, these systems foster a culture of accountability among employees.
Scalability
RFID Key Management Systems are highly scalable, making them suitable for businesses of all sizes. They can handle an extensive number of keys and users, allowing businesses to expand their operations without having to worry about outgrowing their key management system.
Real-Time Tracking and Alerts

Most RFID Key Management Systems offer real-time tracking capabilities. If a key isn’t returned within a specified time, the system can send an alert to the administrator, thereby minimizing the risk of lost or misplaced keys. Similarly, if an attempt is made to remove a key without authorization, an immediate alert can be triggered, thereby enhancing the security of the premises.
By offering these benefits, RFID Key Management Systems represent a significant advancement in access control technology. They provide a flexible, secure, and efficient solution to manage keys, thereby simplifying operations while enhancing security.
Use Cases of RFID Key Management System
RFID Key Management Systems find wide application across various industries, like healthcare, retail, logistics, and more. They have shown effectiveness in managing access and promoting overall security in these sectors.
Residential Buildings

In residential complexes, such as apartment buildings and gated communities, RFID Key Management Systems can offer a high level of security. They can control access to communal areas such as gyms, swimming pools, and lounges, ensuring only residents or authorized individuals can access these facilities. This helps to maintain a safe and secure living environment for all residents.
Furthermore, RFID systems can be used to manage guest access, allow secure parcel deliveries, and even track maintenance personnel within the property. This system can provide residents with peace of mind knowing who has access to their building and when.
Commercial Buildings

Commercial buildings often have complex access requirements due to the diversity of occupants and the sensitivity of certain areas. From office buildings to shopping malls, RFID Key Management Systems can ensure secure and efficient access control.
In office buildings, these systems can control access to various areas based on employee credentials. They can help restrict access to sensitive areas such as server rooms, financial departments, or executive suites, thereby enhancing the overall security of the building. Furthermore, they can keep accurate records of who accessed what areas at which times, thereby fostering a culture of accountability.
In shopping malls, RFID Key Management Systems can secure access to storage areas, cash offices, and other sensitive locations. They can help prevent theft and facilitate smoother operations by ensuring that only authorized personnel can access these areas.
Healthcare
RFID Key Management Systems are indispensable in healthcare facilities. From tracking access to drug cabinets to monitoring the usage of high-value equipment, these systems ensure that only authorized personnel can access specific areas and resources. This is crucial for patient safety, data privacy, and compliance with regulatory standards.
Education
In educational institutions, RFID Key Management Systems provide an additional layer of security. They can control access to classrooms, labs, libraries, and other facilities, ensuring that only authorized personnel and students can access these areas. They can also be used to track the usage of shared resources, such as projectors or laboratory equipment.
Retail
In the retail industry, RFID Key Management Systems are used to secure storage rooms, cash offices, and other sensitive areas. They can help prevent theft, both from customers and employees, by ensuring that only authorized individuals can access these areas. They can also provide valuable data for loss prevention analysis.
Government Facilities
Government buildings often have high-security requirements. RFID Key Management Systems can control access to sensitive areas, protect classified information, and ensure the integrity of the operations. They can also assist in compliance with government-mandated security regulations.
Hospitality
Hotels, resorts, and Airbnb facilities can use RFID Key Management Systems to enhance guest experience while improving operational efficiency. They can control access to guest rooms, spas, fitness centers, and other facilities. They can also track the usage of hotel amenities, aiding in inventory management and maintenance scheduling.
Logistics and Supply Chain
RFID Key Management Systems can significantly enhance the efficiency of logistics operations. They can be used to control access to warehouses, track the movement of goods, and monitor the usage of delivery vehicles. This can lead to improved inventory management, timely deliveries, and overall operational efficiency.
These examples underscore the versatility of RFID Key Management Systems. Across various sectors, these systems are revolutionizing the way businesses manage access control, leading to improved security, accountability, and operational efficiency.
Choosing the Right RFID Key Management System
BAS-IP Link brings a plethora of features that cater to the dynamic needs of different properties, be it residential, commercial, or public buildings. Here’s why BAS-IP Link can be the right choice:
- Versatile Integration: BAS-IP Link can seamlessly integrate with any BAS-IP hardware, such as door entry panels and access control readers. This compatibility ensures a smooth and unified access control operation.
- Data Security: Offering a robust backup and restore system, BAS-IP Link prioritizes data security. Regular backups can be taken to prevent data loss, ensuring information is always safe and readily restorable.
- Flexible Installation Options: Whether you prioritize privacy or accessibility, BAS-IP Link has got you covered. It can be installed locally on your property or in any cloud storage, catering to your unique requirements.
- Cross-Device Functionality: BAS-IP Link is designed to be accessible from a computer, tablet, or iOS/Android mobile device. This means you can manage and monitor your property’s access control system from virtually anywhere.
- Comprehensive System Logging: With BAS-IP Link, you get extensive system logging and managing capabilities. This feature is invaluable for tracking usage, spotting irregularities, and maintaining overall security.
- Face ID Support: Incorporating modern biometric technology, BAS-IP Link supports Face ID. This feature allows for touchless and secure access, enhancing the convenience and security of property access.
- Tailored User Permissions: BAS-IP Link offers various user types: Administrator, Concierge, and User, each with their own set of administration options. This customization enables effective management while maintaining clear responsibility boundaries.
Given these factors, it’s clear that BAS-IP Link provides a comprehensive, versatile, and secure RFID Key Management System solution suitable for a wide range of properties.
Below is a simple chart that highlights the key features of BAS-IP Link:
| Feature | Benefit |
|---|---|
| Versatile Integration | Seamless operation with BAS-IP hardware |
| Data Security | Robust backup and restore system |
| Flexible Installation Options | Local or cloud installation for customized privacy and accessibility |
| Cross-Device Functionality | Manage from computer, tablet, or mobile device |
| Comprehensive System Logging | Track usage and maintain security |
| Face ID Support | Touchless and secure access |
| Tailored User Permissions | Effective management with clear responsibility boundaries |
This comprehensive suite of features makes BAS-IP Link a top choice when it comes to choosing an RFID Key Management System for your property.
Implementing an RFID Key Management System
Implementation of an RFID Key Management System involves meticulous planning and execution. While the process may pose challenges, the right preparation and expert assistance can smooth the transition.
Needs Assessment and System Planning
Begin by assessing your current access control needs, taking into account the scale and structure of your property. This will help you understand how the BAS-IP Link system can be tailored to meet your unique needs.
Choosing Your Setup
Decide whether you want to install Link locally or in the cloud. Both setups have their advantages: a local setup may provide you with more control and data security, while a cloud setup could offer more accessibility and ease of scalability.
Hardware Installation
Connect your BAS-IP hardware, including door entry panels and access control readers, to your chosen system setup. Make sure all hardware is installed correctly and is communicating effectively with the Link system.
Software Configuration
Once your hardware is installed, configure the BAS-IP Link software. This includes setting up different user types (Administrator / Property Manager, Concierge, User) and assigning them the appropriate administration options based on their roles and responsibilities.
Face ID Setup
If you wish to use the Face ID feature, this will need to be configured. You will need to enroll authorized individuals by capturing their face images into the system.
System Logging and Management
Establish your logging preferences within the system. BAS-IP Link provides comprehensive system logging, which can be valuable for tracking usage, troubleshooting problems, and maintaining security.
Backup and Restore System Setup
Set up the backup and information restore system provided by BAS-IP Link. Regular backups will ensure that your data is safe and can be restored quickly in case of any data loss.
Training
Train all users on how to use the BAS-IP Link system. This includes administrators, concierges, and users. Make sure they understand the functionality and responsibilities associated with their specific user type.
Testing and Adjustment
Finally, thoroughly test the entire system to ensure that everything is working as expected. Make any necessary adjustments based on the results of your testing.
Implementing an RFID Key Management System like BAS-IP Link can significantly enhance your property’s access control. However, proper planning, installation, and training are crucial to ensure the system’s successful deployment and operation.
Future of RFID Key Management Systems
The future of RFID Key Management Systems looks promising. With technological advancements, we can expect more features, better integration, and improved performance from these systems.
Conclusion
RFID Key Management Systems are revolutionizing access control, bringing about a shift towards secure and efficient operations. As technology evolves, we are sure to witness even more enhanced systems in the future. What do you think about the future of RFID Key Management Systems? Share your thoughts in the comments below!

