Wiegand Protocol in Access Control: Unlock Exceptional Security

The Wiegand Protocol in Access Control has become a pivotal component in any modern door entry system, offering a unique and secure communication method that ensures the safety and efficiency of various operations. In this comprehensive guide, we’ll dive deep into the world of Wiegand, exploring its inner workings, applications, and benefits. From intercom systems to heating and cooling solutions, the Wiegand protocol proves to be a versatile and essential tool in today’s world.
Table of Contents
What is Wiegand Protocol?
The Wiegand protocol is an electronic communication system that allows for secure data transmission between devices. Developed in the late 20th century by John Wiegand, this protocol has become the industry standard for access control, with its high reliability and robust security features.
How Does the Wiegand Protocol Work?
At the heart of the Wiegand protocol are Wiegand wires, which are responsible for transmitting data between devices, such as keypads, card readers, and controllers. The data transmitted consists of binary code, utilizing a combination of voltage levels and timing to convey the necessary information securely.
| Parameter | Description | Example |
|---|---|---|
| Signal | Electrical voltage and timing characteristics of the Wiegand protocol | Voltage levels: 0V (Low) and 5V (High) |
| Data | Binary information transmitted between devices using Wiegand wires | 101001101000111010 |
| Leading Parity Bit (LPB) | A single bit used for error checking; even parity for Wiegand protocol | 1 (even parity) |
| Facility Code | A unique identification code assigned to an organization or facility | 10110 (decimal: 22) |
This chart illustrates the key elements of the Wiegand protocol’s signal and data transmission, showcasing the importance of the facility code and error-checking mechanisms like the leading parity bit (LPB) to ensure secure and accurate communication.
Wiegand Keypad and Reader Applications
Wiegand keypads and readers have found their way into various industries, making them a versatile solution for secure access control.
Intercom Systems
In the realm of intercom systems, the Wiegand protocol in access control ensures secure communication between the keypad and the main controller, enabling a seamless and secure operation in various settings, including residential, commercial, and industrial environments.
BAS-IP Intercom Door Entry Panels with Wiegand Integration
BAS-IP, a leading intercom systems manufacturer, offers advanced door entry panels that seamlessly integrate with the Wiegand protocol. These panels are designed to provide secure access control while maintaining a high level of versatility. Equipped with both Wiegand input and output, the BAS-IP panels support a wide range of Wiegand card formats, including Wiegand-26, 32, 34, 37, 40, 42, 56, 58, and 64. This flexibility allows organizations to select the ideal format based on their security requirements and user population, ultimately providing a tailor-made solution that meets the needs of various industries and applications. With the combination of BAS-IP’s innovative intercom technology and the robust Wiegand protocol, these door entry panels deliver exceptional performance, security, and ease of use.
Security and Access Control
The Wiegand protocol is frequently used in security systems, including door access controls and gates. With its high level of security, the protocol effectively prevents unauthorized access, ensuring the safety of both people and property.
Wiegand Heating and Cooling Integration
Beyond access control, the Wiegand protocol can be integrated into heating and cooling systems, providing intelligent temperature control and energy efficiency.
Smart Thermostats
By incorporating Wiegand technology, smart thermostats can communicate with other devices, adjusting the temperature based on occupancy and access patterns, ultimately resulting in energy savings and a more comfortable environment.
Wiegand Wiring Diagram and Interface
The Wiegand wiring diagram showcases the intricate interconnections between the various devices, including keypads, readers, and controllers. Understanding the wiring diagram is essential for the correct installation and configuration of a Wiegand-based system.
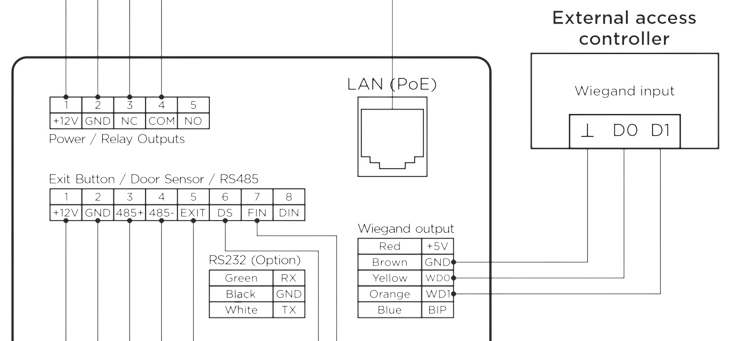
Components of a Wiegand Interface
The Wiegand interface comprises several components that work together to facilitate secure data transmission:
- Wiegand Reader: A device that reads information from access cards, key fobs, or other input methods.
- Wiegand Keypad: A manual input device that allows users to enter credentials for access.
- Wiegand Controller: The central component that processes the transmitted data and manages the entire system.
Wiegand Access Control and Card Formats
The Wiegand protocol supports various card formats, each with unique features that cater to different access control requirements.
Most Common Formats
Wiegand 26-Bit Card Format
The 26-bit Wiegand card format is the most common and widely used, offering a balance between security and ease of use. This format consists of 26 bits of binary data, with 24 bits dedicated to the user’s unique identification code and two bits reserved for parity checking.
Wiegand 37-Bit Card Format
The 37-bit Wiegand card format offers an even higher level of security, with 35 bits dedicated to the user’s unique identification code and two bits for parity checking. Due to its increased data capacity, this format is ideal for organizations with a larger number of users or more complex access control requirements.
All Wiegand Formats Supported by BAS-IP Intercoms
| Wiegand Format | Total Bits | Facility Code Bits | Unique ID Bits | Parity Bits | Applications |
|---|---|---|---|---|---|
| Wiegand-26 | 26 | 8 | 16 | 2 | Most common access control |
| Wiegand-32 | 32 | 10 | 20 | 2 | Medium-sized organizations |
| Wiegand-34 | 34 | 12 | 20 | 2 | Larger organizations |
| Wiegand-37 | 37 | 15 | 20 | 2 | Enhanced security requirements |
| Wiegand-40 | 40 | 16 | 22 | 2 | Specialized access control |
| Wiegand-42 | 42 | 18 | 22 | 2 | Advanced security features |
| Wiegand-56 | 56 | 24 | 30 | 2 | High-security applications |
| Wiegand-58 | 58 | 26 | 30 | 2 | Complex systems & large user base |
| Wiegand-64 | 64 | 30 | 32 | 2 | Maximum security & flexibility |
This comparison chart showcases the key differences between various Wiegand protocol formats, highlighting the number of bits allocated for facility codes, unique IDs, and parity bits. Each format is suited for different applications, ranging from standard access control to maximum security and flexibility.
Exploring Wiegand Protocol Benefits
The Wiegand protocol has earned its reputation in the world of access control, and for good reason. Here, we’ll discuss the key benefits of implementing Wiegand-based systems.
High Security
One of the primary advantages of the Wiegand protocol is its robust security features, ensuring that unauthorized access is prevented and sensitive data remains protected.
Reliability
The Wiegand protocol is known for its exceptional reliability, making it a preferred choice for critical systems where stability and accuracy are of utmost importance.
Versatility
The Wiegand protocol’s adaptability allows it to be applied to various industries and systems, including intercom systems, security access control, and heating and cooling management.
Frequently Asked Questions (FAQs)
Conclusion
The Wiegand protocol has revolutionized access control systems and other industries, offering a secure, reliable, and versatile communication method. Its applications extend from intercom systems to heating and cooling management, demonstrating the protocol’s adaptability and value. By understanding and implementing Wiegand-based systems, organizations can enhance security, efficiency, and overall performance in today’s fast-paced, interconnected world.